Intel SGX
Intel SGX provides a set of CPU instructions to create an Enclave, an area of confidentiality and integrity. SGX ensures that confidential data is correctly processed and protected, even during attacks at the OS, VMM, and other layers.
An application using Intel SGX consists of an Enclave, a trusted area, and a Host Application, an untrusted area, as follows:
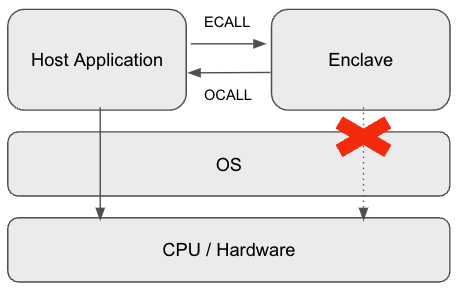
The Host Application can access the Enclave only through ecall. Enclave can call the Application side by using ocall.
The main elements of SGX are as follows.
MRENCLAVE
MRENCLAVE is one of the enclave measurements to check the validity of Enclave software. It is a cryptographic hash of the program executed in the enclave, specifically, binary, stack, heap, and log including environment variables. Parties need to obtain this value securely for verification.
Sealing
SGX supports a mechanism to obtain a key unique to an Enclave to protect and store data outside the Enclave permanently. Encryption and decryption using this key are called "seal" and "unseal," respectively.
Architectural Enclave(AE)
SGX provides several enclaves, called Architectural Enclaves (AE) including one for handling the launch of other enclaves and one that enables attestation for the validity of enclaves.
Quote
Quote is a struct signed by Quoting Enclave (QE), one of the AEs, for hardware information called Report and enclave information such as MRENCLAVE. The QE also uses the Attestation Key (AK) as the signature key. There are two types of signature schemes: Enhanced Privacy ID (EPID) and ECDSA.
Remote Attestation
Intel SGX provides Remote Attestation, which allows remote parties to verify the validity of hardware and enclaves.
Two types of Remote Attestation schemes currently exist in SGX, each corresponding to a signature scheme in Quote. One is EPID-based attestation, which allows attestation while preserving platform anonymity. In this case, only the Intel Attestation Service(IAS) can verify the Quote. Therefore, the remote party verifies the signature on the IAS's verification report containing the Quote. The other is ECDSA-based attestation, which is used with a package called DCAP, mainly for data centers and Cloud Service Providers, and allows remote party verification without an external Attestation Service. We define a Quote that can be verified by the remote party as a Verifiable Quote, regardless of the Attestation method. The IAS's Attestation Verification Report is an example of a Verifiable Quote.