LCP Client (zkDCAP)
Overview
The LCP Client (zkDCAP) extends the LCP Client (IAS) by supporting DCAP (Data Center Attestation Primitives) Remote Attestation using zkDCAP, a technology to efficiently verify SGX/TDX quotes on-chain using ZKP.
This client is intended to be implemented as a Light Client module in ibc-go or ibc-solidity, conforming to ICS-02.
Differences from LCP Client (IAS)
The primary difference is the addition of the zkDCAPRegisterEnclaveKey function to handle zkDCAP verification. Other functions remain as described in the LCP Client (IAS) documentation.
zkDCAP Overview
Verifying DCAP quotes directly on Ethereum or other EVM-compatible chains consumes significant gas. To address this, we developed zkDCAP, a solution that offloads the quote verification process to an off-chain zkVM (RISC Zero) and generates a zero-knowledge proof (ZKP) of the verification result.
The LCP Client integrates zkDCAP in a way that minimizes trust assumptions: under the design of the ZKP verifier and the TCB evaluation logic, verification remains secure as long as at least one operator fetches the latest TCB data from Intel Provisioning Certification Service (PCS).
The following diagram illustrates the end-to-end flow of enclave key (EK) registration using zkDCAP. It shows how a quote is generated by an SGX/TDX platform, verified off-chain by the zkDCAP guest program on the RISC Zero zkVM, and how the resulting output and proof are submitted to the LCP Client for verification and registration.
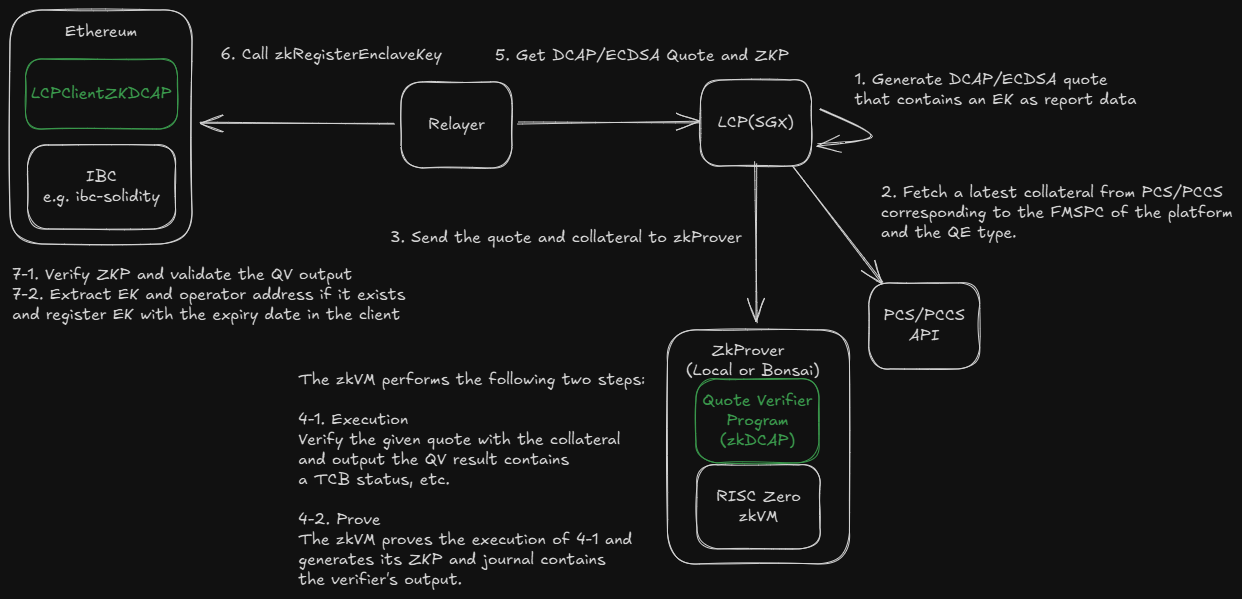
For further details on how zkDCAP works, see the zkDCAP README.
State Definition
ClientState
message ClientState {
bytes mrenclave = 1;
uint64 key_expiration = 2;
bool frozen = 3;
Height latest_height = 4;
repeated string allowed_quote_statuses = 5;
repeated string allowed_advisory_ids = 6;
repeated bytes operators = 7;
uint64 operators_nonce = 8;
uint64 operators_threshold_numerator = 9;
uint64 operators_threshold_denominator = 10;
// New fields for zkDCAP
uint32 current_tcb_evaluation_data_number = 11;
uint32 tcb_evaluation_data_number_update_grace_period = 12;
uint32 next_tcb_evaluation_data_number = 13;
uint64 next_tcb_evaluation_data_number_update_time = 14;
repeated bytes zkdcap_verifier_infos = 15;
}
current_tcb_evaluation_data_numberspecifies the minimum TCB evaluation data number that the client currently accepts. zkDCAP outputs are accepted only if they are generated using collateral with a TCB evaluation data number equal to or greater than this value.tcb_evaluation_data_number_update_grace_periodspecifies a grace period (in seconds) allowing operators sufficient time to update their SGX environments when a new TCB evaluation data number is observed.next_tcb_evaluation_data_numberholds the upcoming TCB evaluation data number scheduled to replace the current one after the grace period.next_tcb_evaluation_data_number_update_timeis the UNIX timestamp when thenext_tcb_evaluation_data_numberbecomes active.zkdcap_verifier_infoscontains verifier-specific data required by zkDCAP, including zkVM type identifiers and zkVM-specific information.
Please refer to the the ClientState definition for the details.
ConsensusState
Remains identical to the existing LCP Client (IAS).
ZKDCAPRegisterEnclaveKey
ZKDCAPRegisterEnclaveKey is a function that validates a zkDCAP output and its proof and registers an enclave key (EK) generated by an SGX enclave running on a secure platform. Currently, this client supports only the RISC Zero zkVM for proof verification.
The function signature is defined as follows:
function zkDCAPRegisterEnclaveKey(string calldata clientId, ZKDCAPRegisterEnclaveKeyMessage calldata message)
The ZKDCAPRegisterEnclaveKeyMessage contains the necessary data for validating and registering the enclave key. Its structure is defined as:
message ZKDCAPRegisterEnclaveKeyMessage {
uint32 zkvm_type = 1; // Identifier for the zkVM type generating the proof
bytes quote_verification_output = 2; // The zkDCAP verification output
bytes proof = 3; // ZKP generated by zkVM for the verification output
bytes operator_signature = 4; // Optional EIP-712 operator signature
}
zkDCAP Quote Verification Output
The quote_verification_output is a structured output produced by the zkDCAP Quote Verifier. It contains the following values required for on-chain verification:
sgxIntelRootCAHash: Hash of the Intel Root CA certificate used in collateral verification.tcbStatus: TCB status of the target platform and the enclaveadvisoryIDs: Security advisory IDs relevant to the target platform or Quoting Enclave (QE).validityNotBeforeandvalidityNotAfter: Validity period for the collateral.min_tcb_evaluation_data_number: The minimum TCB evaluation data number of the collateral used in verification.mrenclave: Enclave measurement identifying the enclave. This value can be extracted fromquote_body.enclaveDebugEnabled: Indicates whether the enclave was operating in debug mode. This value can be extracted fromquote_body.
For further details, refer to the zkDCAP repository.
zkDCAP Output Validation
- Proof Verification: Using the RISC Zero zkVM verifier contract, it verifies the provided ZKP against the
quote_verification_output. - zkDCAP Output Validation: The output is parsed to confirm:
- The parsed
sgxIntelRootCAHashmatches the expected Intel Root CA hash stored in the client. mrenclavematches the one stored inClientState.- The
tcbStatusis either "UpToDate" or explicitly allowed in the client'sallowed_quote_statuses. - All security advisories listed in
advisoryIDsare explicitly allowed in the client'sallowed_advisory_ids. - The current block timestamp is within the validity range (
validityNotBefore,validityNotAfter). - The enclave debug mode (
enclaveDebugEnabled) matches the client's configureddevelopmentMode. - The
min_tcb_evaluation_data_numberfrom the verification output is equal to or greater than the client'scurrent_tcb_evaluation_data_number.
- The parsed
- EK Expiration Calculation: Calculates the EK expiration timestamp (
expiredAt) based onkey_expiration:- If
key_expirationis0, the EK expires atvalidityNotAfter. - Otherwise, the EK expiration is the minimum between
validityNotBefore + key_expirationandvalidityNotAfter.
- If
- Operator Signature Verification: If an operator signature (
operator_signature) is provided, verify it matches the operator address associated with the enclave key.
Security Assumptions
The security and reliability of the LCP client protocol are based on the following assumptions about operators (not limited to those listed in the client state's operators field):
TCB Data Synchronization: At least one operator regularly fetches and uses the latest TCB evaluation data from Intel's Provisioning Certification Service (PCS) to ensure synchronization with actual TCB recovery events. Without this assumption, the client could potentially accept attestations evaluated with outdated TCB collateral for up to 12 months (Note: See also the Intel PCS documentation on the
update=standardparameter).SGX Platform Upgrade Readiness: Operators must maintain readiness to promptly upgrade their SGX platforms when a new TCB evaluation data number is observed. Operators should set an appropriate grace period allowing sufficient time for these platform upgrades. This grace period represents a trade-off—longer periods can delay adopting the latest TCB data (increasing security risks), while shorter periods could risk availability if operators cannot complete upgrades promptly.
TCB Evaluation Management
Under the operational assumptions, TCB evaluation data numbers (client's current_tcb_evaluation_data_number and next_tcb_evaluation_data_number, min_tcb_evaluation_data_number from zkDCAP's Quote Verification Output) are managed as follows:
General Cases:
Scheduled Update:
- If the grace period is non-zero, and no next TCB number is reserved, the newly observed
min_tcb_evaluation_data_numbergreater than the current is reserved asnext_tcb_evaluation_data_number, scheduled for activation after the defined grace period.
- If the grace period is non-zero, and no next TCB number is reserved, the newly observed
Immediate Update:
- If the grace period is zero, immediately update
current_tcb_evaluation_data_numberwhen a highermin_tcb_evaluation_data_numberis observed. - If the grace period is non-zero and the current time exceeds the scheduled
next_tcb_evaluation_data_number_update_time, immediately activate the reservednext_tcb_evaluation_data_numberas the current number.
- If the grace period is zero, immediately update
However, the following edge cases may occur:
Edge Cases:
- Edge case 1 (
current < next reserved < newly observed): Immediately activate the reserved next number as the current number, bypassing any remaining grace period, and schedule the newly observed number as next. - Edge case 2 (
current < newly observed < next reserved): Immediately update the current number to the newly observed number, keeping the existing reserved number unchanged.
We assume that these edge cases represent immediate updates to non-latest TCB numbers, which do not pose issues due to the operational assumption that operators maintain readiness and utilize up-to-date or near-current TCB collateral.
State Management and Events
Upon successful validation:
- The enclave key (EK) is stored with:
expiredAt: Calculated expiration timestamp.operator: Associated operator address (if provided).
- TCB evaluation data numbers are updated according to the described rules.
- The enclave key (EK) is stored with:
Events emitted:
LCPClientZKDCAPRegisteredEnclaveKey: Emitted upon successful EK registration, containing:clientId: Client identifier.enclaveKey: Ethereum address format of EK.expiredAt: EK expiration timestamp.operator: Associated operator address (if not provided, set to the zero address).
LCPClientZKDCAPUpdateCurrentTcbEvaluationDataNumber: Emitted whencurrent_tcb_evaluation_data_numberis updated.LCPClientZKDCAPUpdateNextTcbEvaluationDataNumber: Emitted when a newnext_tcb_evaluation_data_numberis scheduled.
Reference Implementation
Security Audit
The LCP Client, including its integration with zkDCAP, was audited by Quantstamp.
The audit covered critical logic such as enclave key registration, TCB evaluation management, and the verification of zero-knowledge proofs on-chain.
You can find the full audit report here: https://certificate.quantstamp.com/full/datachain-lcp-zk-dcap/15bac7cd-3b90-47c7-a25e-b0c3214c6630/index.html